CLOUD SECURITY POSTURE MANAGEMENT
CLOUD SECURITY WITH INTEGRATED RISK & THREAT VISIBILITY, CONTROL, & AUTOMATED PROTECTION
Ztech’s revolutionary cloud security solutions offer a continuous assessment of risk and automated enforcement of an organization’s hardened security policies and configurations to reduce risk proactively. In addition to continuously assessing risk, we also incorporate global threat intelligence, active threats, and your organization’s current threat landscape to adaptively adjust “trust”— access, privileges, and controls within your cloud environments.
The breakthrough of Ztech’s Cloud Security Posture Management (CSPM) solution is its ability to surgically adapt individual or group access and privileges based on their behaviors and the severity of a threat, maintaining productivity and workflows while protecting your cloud environments.

MULTI-CLOUD VISIBILITY
Risk protection & threat detection for SaaS and IaaS environments

COMPLIANCE ADHERENCE
24/7 Automated enforcement & configuration of security policies

AGILE & EFFECTIVE
Reliable security without impacting speed or performance
of organizations store some of all of their sensitive data in public cloud environments
of today’s IT support is deof cloud breaches were the result of misconfigurations or mistakeslivered remotely
PUT AN END TO THE STRUGGLE OF MEASURING SECURITY RISKS WITH UNIFIED VISIBILITY AND ZTECH’S CLOUD & SECURITY EXPERTS.
CONTINUOUS VISIBILITY INTO AN ARRAY OF CLOUD ENVIRONMENTS
Cloud Security Posture Management (CSPM) automates security management across the following diverse infrastructure:
Software as a Service (SaaS) – Ztech performs comprehensive assessments of client SaaS environments, as well as real-time configuration management. Ztech’s highly-trained and certified Security Operations Center (SOC) team tracks your security posture in real-time and ensures the appropriate configuration of your cloud applications such as Office 365.
Platform as a Service (PaaS) Risk Protection – Ztech source integrates with Amazon Web Services and Microsoft Azure to monitor and detect threats against application framework. Using a customized risk management plan, we automatically assess those assets and provide reports or notifications, and coordinate assessment activities according to your organization’s unique needs. Ztech source also provides container risk discovery services to measure a container’s security against custom or Center for Internet Security (CIS) policy definitions.
Infrastructure as a Service (IaaS) Risk Protection – Visibility into cloud workloads is critical to ensuring the security of your cloud environment. Using a customized risk management plan, we automatically assess system configuration against CIS benchmark standards via API and Ztech source’s CSPM agent.
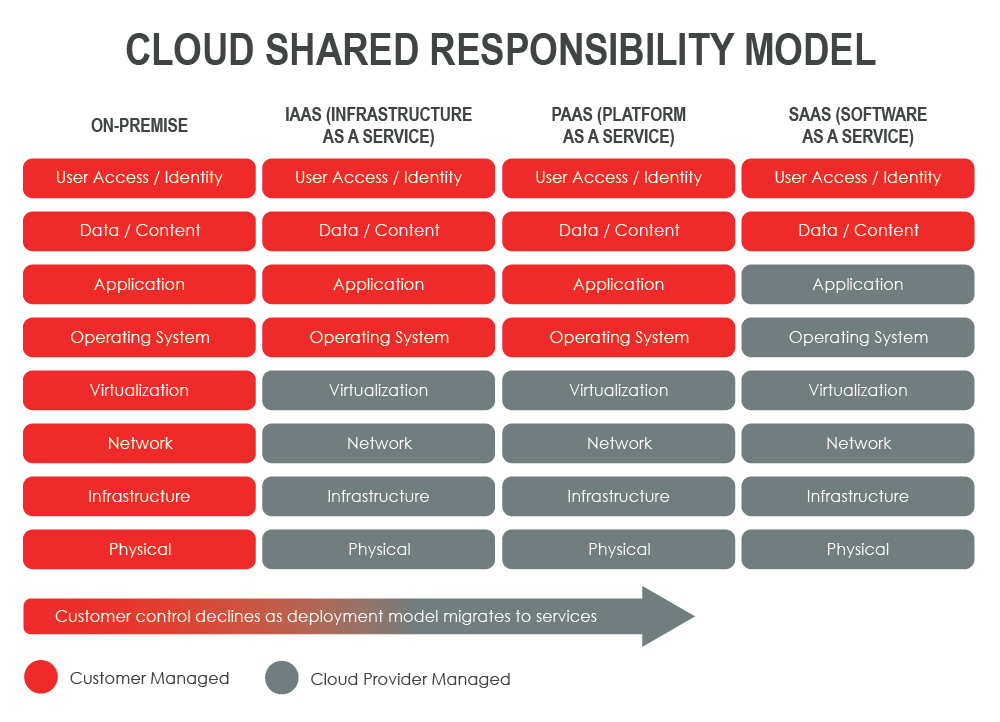
UNDERSTANDING THE GRAY AREAS OF THE SHARED RESPONSIBILITY MODEL
After moving to the cloud, many organizations mistakenly assume their cloud hosting provider is entirely responsible for security. This mistaken belief leads to data breaches and other security mishaps. Through 2025, Gartner predicts that 99% of security failures in a cloud environment will be the public cloud customer’s fault.